This is an example post




This is an example post
An increasing number of businesses are embracing the ‘bring your own device’ policy, allowing employees to use their smartphones and tablets to access the company’s information and work on the go.
This policy can add a new dimension to IT project management training, with products now able to be developed remotely and flexibly using mobile devices. However, it also means that a greater emphasis now needs to be placed on mobile cyber security to ensure that businesses are keeping their information secure.
Threats being detected in the Android app store
Although all kind of devices has risks associated with them, those operating on the Android platform are shown to be particularly vulnerable to malware from apps. It’s therefore essential that companies with employees using Android devices are extra vigilant and aware of the possible threats.
The most prominent threat to Android users is apps, with the Google Play Store being invaded by numerous applications containing malware. Google Play Protect detected and removed 1,700 Android apps infected with the malware Bread (also known as Joker) before ever being downloaded by users.
Likewise, an analysis by G DATA showed that the number of malicious apps reached a record level in 2019. This problem is growing, and businesses have to look out for ransomware and Trojans that might compromise their data for money.

How can businesses protect themselves?
Due to the magnitude of this risk, it’s important for businesses to know the security measures they should take to defend employees mobile devices from malware. Lukas Stefanko, expert at security solutions company ESET, emphasises that the best approach to security is preventative.
“Don’t delay taking security measures until something unusual happens – in most cases it’s too late as the device may already be compromised and the data lost,” he said in an interview with We Live Security.
Businesses should require that all employees using their personal devices to access company information to have the latest operating system and antivirus software installed to defend against cyber threats. They should also encourage people to be careful of the apps they download, and always check the reviews before installing anything.
It is apparent how mobile security has become an integral aspect of information security training, and companies need to ensure they protect all channels of data access. ALC Training can help by educating employees in all aspects of cyber security, resulting in better protection for businesses in the long run.
Source:
Google Security Blog – Read the full details here .
Digital Transformation is the ability of an organisation to remain competitive. By using new technologies more effectively than their competitors, this leads to greater market share, lower price points, improved product and/or service quality and constant innovation for clients. But where do you start?
This article is designed for medium to large organisations that want to know how to do this. I’ll draw on my 20 years of experience as an enterprise and solution architect with DXC technology. I was fortunate enough to help a range of clients which I can now couple with my knowledge as a trainer, across the 12+ courses that I now run.
Click to open the infographic below to see a snapshot of the steps to take to perform a digital transformation successfully.
Here is my list of key steps in order:
Do you have questions with these steps? Contact our awesome ALC Training team!
I have been in the infosec sector for over three decades and have seen the rise and fall of demand for IT and security professionals on a number of occasions. Y2K, the dot com bust and the GFC did not help our industry. Currently, we are on an upward trend, delivering training across Australia, NZ, Malaysia, Singapore and Dubai. I have seen year-on-year growth as people take up the call to either upskill, try to get a foot in the door or just learn about on-trend topics, such as cyber security, architecture, cloud, big data, artificial intelligence, digital forensics or incident response.
ALC recently added privacy to our portfolio by partnering with the International Association of Privacy Professionals (IAPP) and we’re making great inroads due to the pent-up demand in Australia and New Zealand. At the recent IAPP conference, the key message emerging from presenters, is one of accountability – having a key individual within an organisation drive the privacy agenda forward; it is all about privacy by design. And no wonder, every week, there is an article on a new privacy breach, quite often coupled with staff dismissals and a hefty fine.

Our cloud portfolio is also strengthening. ALC made a strategic decision to add Certified Cloud Security Professional (CCSP) to the portfolio in 2017, along with other cloud courses, and Australia now has more certified CCSPs compared to Germany! Running the numbers, we can proudly say we have trained two thirds of those certified in Australia alone. For those who hold a CISSP or have anything to do with cloud, I highly recommend the (ISC)2 CCSP® certification.
So is it all hype, or is there a genuine need for training? In reality, it’s a little hype, but also a genuine need to fill a gap. Increasingly, we have delegates cite several reasons for becoming certified: personal challenge, company requirement, or simply to learn. Many delegates are from organisations that are typically under-resourced when it comes to security and privacy, expecting miracles with existing staff numbers.
Remember, security and privacy are solved by people, process and technology. Therefore, it is everyone’s responsibility. We need effective awareness training and to skill those people on technologies, to look after security in their own domains – rather than expecting a security professional to become a master of all trades. There is a plethora of courses out there to do precisely that.
ALC’s focus is to deliver industry recognised training and certifications that are needed now and into the future. ALC has always been at the forefront of Information Security education since our very first course on Information and System Security in 1995. Our flagship set of courses on SABSA® security architecture and industry standard certifications such as CISSP® and CISM® are designed to meet the needs of the security professional. (FACT: Did you know ALC is an ISACA Training Partner!) Also, in the past three years we’ve placed a very strong focus on addressing the needs of newcomers to Cyber Security to help enable the industry to broaden its skills base with our Cyber Security Foundation+Practitioner Certification.
Cyber Security is a prominent, highly-regarded profession offering many varied career paths. The ALC Cyber Security Portfolio offers a formal route to becoming a recognised and respected cyber security professional through a modular program of certificate and non-certificate courses. Whatever stage you are at in your career, or if you are an Executive in need of improving capabilities within your organisation, we are here to help you, your team or your company, locally and worldwide.
Get in touch with our team to see how we can assist to deliver optimal training suited to your needs.
Peter Nikitser, Director of Cyber Security – ALC
Believe it or not, Office 365 now contains 27 separate apps that are provided by Microsoft. Many of these apps are provided with advanced security features. Clearly managing these security features within each admin tool is a complex and onerous task. So Microsoft have moved as much security as possible into the Office 365 Security & Compliance Centre. This is now the central place to manage the majority of security functions in Office 365.
Click on the diagram below to link to the Microsoft TechNet article describing all the key Office 365 services:
You can augment this list by adding third-party apps that are available in the Microsoft AppSource app store. You can also incorporate various Azure services that integrate with Office. One service that is already included, is Azure Active Directory.
Azure Active Directory or AAD, is a mandatory service that manages all the authentication and authorisations in Office 365. It integrates with your existing corporate Active Directory, which probably lives in your data centre (on-premise), using a service called AAD Connect. For companies that have very complex requirements around transferring data between your on-premise Active Directory and AAD, you can use the Microsoft Identity Manager product and the Active Directory Federation Service.
Here is a great link to a video that outlines some of the basics of Active Directory:
It becomes quite technical towards the end of the video, so just close it down, once you have the knowledge you need.
Understanding Active Directory is key to understanding the fundamentals of how the Office 365 Security & Compliance Centre works, so check out my 2 day course where we cover all the basics, in non-technical language, so that anyone can start security their Office 365 tenancy:
Not only do we cover AAD, but we also run through:
Let’s pick out a couple of my favourite Office 365 services…Flow.
Flow is a product that allows you to integrate various cloud services, providing a platform for automating many of your tasks. It’s a competitor to IFTTT.com, which stands for If This Then That, which provides a similar set of services. For example, if an email comes into your inbox from a customer, there may be a series of manual tasks that need to be undertaken to start servicing that customer. This can be automated and free up your time to focus on talking with customers, rather than having to do repetitive manual tasks.
Click on the graphic to be taken to a video outlining potential uses of the tool:
Now, let’s look at some of the key features of Data Loss Prevention
If want to know more about Office 365 services, please reach out to me on Linkedin. Click on the image below to see my profile and start reaching out….
It may not be obvious, by the concept of a value stream is one of the most important concepts in a digital transformation. Why? Because once you understand a value stream, you start to truly understand your business and you’re on a clear path to improving customer experience. Exceptional customer experience is your key business differentiator in the world of digital disruption and needs to be the core focus of any digital transformation.
Let’s define a value stream. I’ll use what I consider, to be the best sources of knowledge reference.
First from Scaled Agile.
If you click on the image it will take you to the Leading SAFe 2 Day course I run at ALC Training.
Second from the TOGAF certification, written by the Open Group:
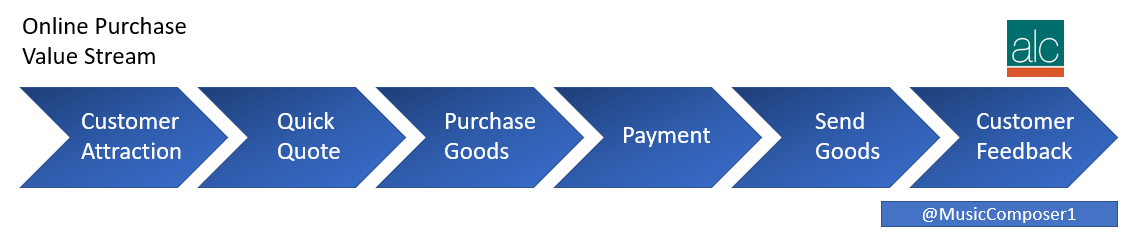
And here is a picture of a sample value stream map for an online purchase:
And here is another, outlining an emergency hospital admission:

As you can see it’s a simple overview, usually shown in 5-9 stages, of how a product or service starts life and is delivered to the consumer.
As you can see, the business processes beneath can vary in complexity. With an online purchase, the process is relatively simple. With say intensive care, the process can be extremely complex and there are probably 1000’s or paths, depending on the type of care required.
It can also be known as:
Clearly, there are many values streams and they are quite different between industries.
Once we understand our value stream, we can then consider decomposing each component into systems and people. An example of this is from Scaled Agile, where they define two types of value streams:
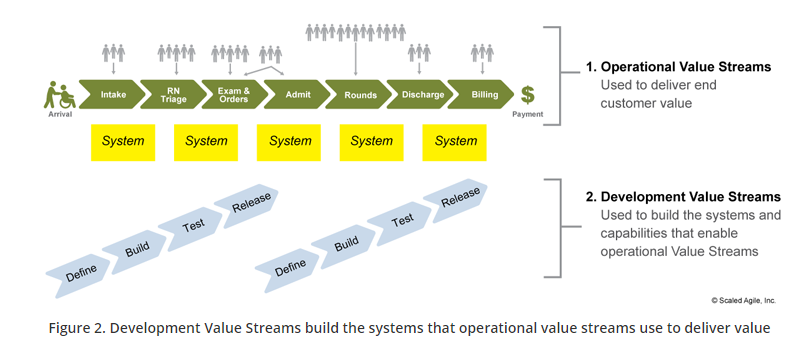
You’ll notice that the operational value stream is the one that is focused on the customer. Whereas the development value stream is aligned to delivering systems in an agile manner. In fact, these are development value streams are also known as a CI/CD pipeline:
So what we’ve now done, is to understand our business in the context of delivering value through software. We cover this in our DevOps Foundation course:
Any questions on Scaled Agile or DevOps concepts, as always please reach out via twitter – @MusicComposer1 or find me on LinkedIn:
There are a number of examples in history, of how governments have fallen. Either through the ballot box, through a coup d’etat or via a civil or military war. But have you ever stopped to think that a lack of progress in a digital transformation, could be a fourth reason?
Let me back up a bit…and outline what I believe are the reasons we have a government. Why does it exist and why we need one. There are five:
Here is a great video that provides some more information on what government is?
Failure by governments to maintain those outcomes and deliver great customer experiences will result in disruption. We’ve already seen this movie before right:
But hey, they’re all commercial examples. Have you got anything that is relevant to government? Sure:
Here is a great video explaining Brexit:
You can also extend that to local government, such as Queensland in Australia:
I talk about digital disruption and governments in the latest #AskTheCEO discussion here:
The same forces that have helped Uber, Netflix, Google and especially Apple become commercial disrupting forces, are the same for the government:
So what is the solution. Well it’s important to understand what needs to transform in government and then do so, quickly. Using the latest Lean-Agile and DevOps principles, along with great talent, is how Spotify undermined their competition, so government needs to do the same. Here are three examples:
Interesting in learning more about digital transformation. Check out a range of courses that I run at ALC Training:
DevOps Foundation
Cloud Security
Cloud Computing
Scaled Agile
Enterprise Big Data

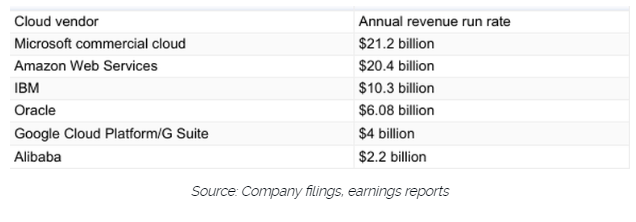
Microsoft is one of the world leaders when it comes to cloud computing services. In the last comparison of revenue streams from the cloud giants, back in Feb 2018, it seems that Microsoft was just ahead in front of AWS.
Want to learn more about Azure? Well, there are options. There is a great free resource from Microsoft that covers Azure fundamentals here:
https://docs.microsoft.com/en-us/learn/paths/azure-fundamentals/
Or, if you’re looking for more a hands-on 1 Day Azure Technical Quickstart to understand how to provision resources, you can check out our 1 Day course here:
https://alctraining.com.au/course/microsoft-azure-technical-quickstart/

You can also reach out to us, for customised Azure and Office 365 courses.
Azure is classed as an Infrastructure-As-A-Service (Iaas) and Platform-As-A-Service (PaaS) in the cloud computing world. IaaS services are designed for system engineers, where you can set up and build servers, networks, and storage, and then install your apps on top. If you’re in the software development business, then the PaaS services are designed for writing, testing and managing code, and target developers.
Some important PaaS services that developers will need include:
Below is a brief snapshot of just the Compute services:
By combining together these services, you can create a rich tapestry of solutions. It’s very similar to the age of analog electronics, where you could select oscillators, diodes and specific electronics components, to create solutions like creating a home radio.
In Azure you can create very complex business solutions. Below is an example of how you might integrate a complex corporate environment with Azure services, in a model known as hybrid cloud:
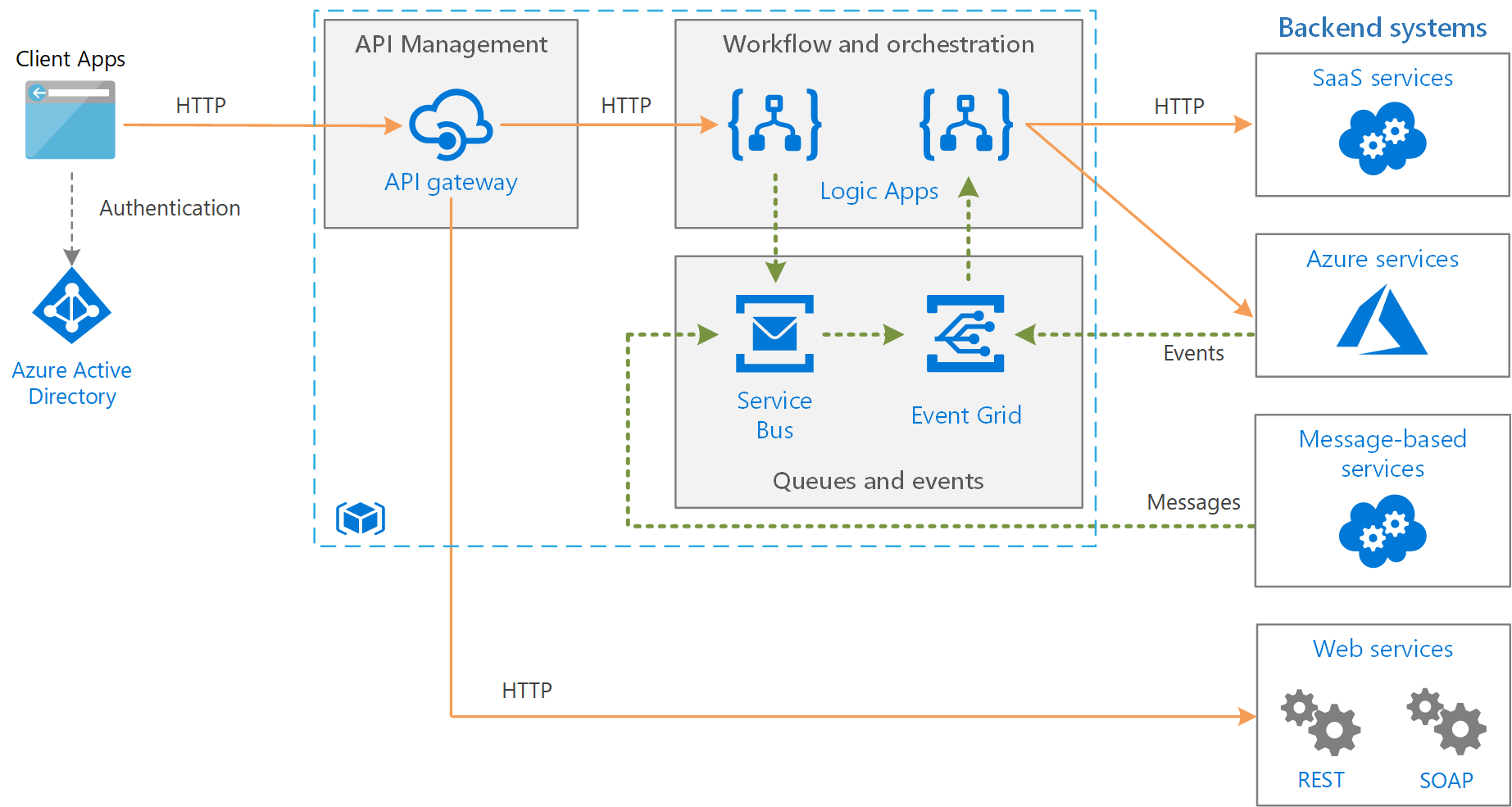
There are some very important services that are available in Azure, that align nicely to medium to large clients that have to comply with complex regulation. Clients involving in banking, government, healthcare, and defence, need to maintain a level of corporate and regulatory governance, as well as a high level of cyber security protection in their cloud services. Tools such as:
The diagram below shows an example of the types of recommendations that the Azure Advisor can provide:
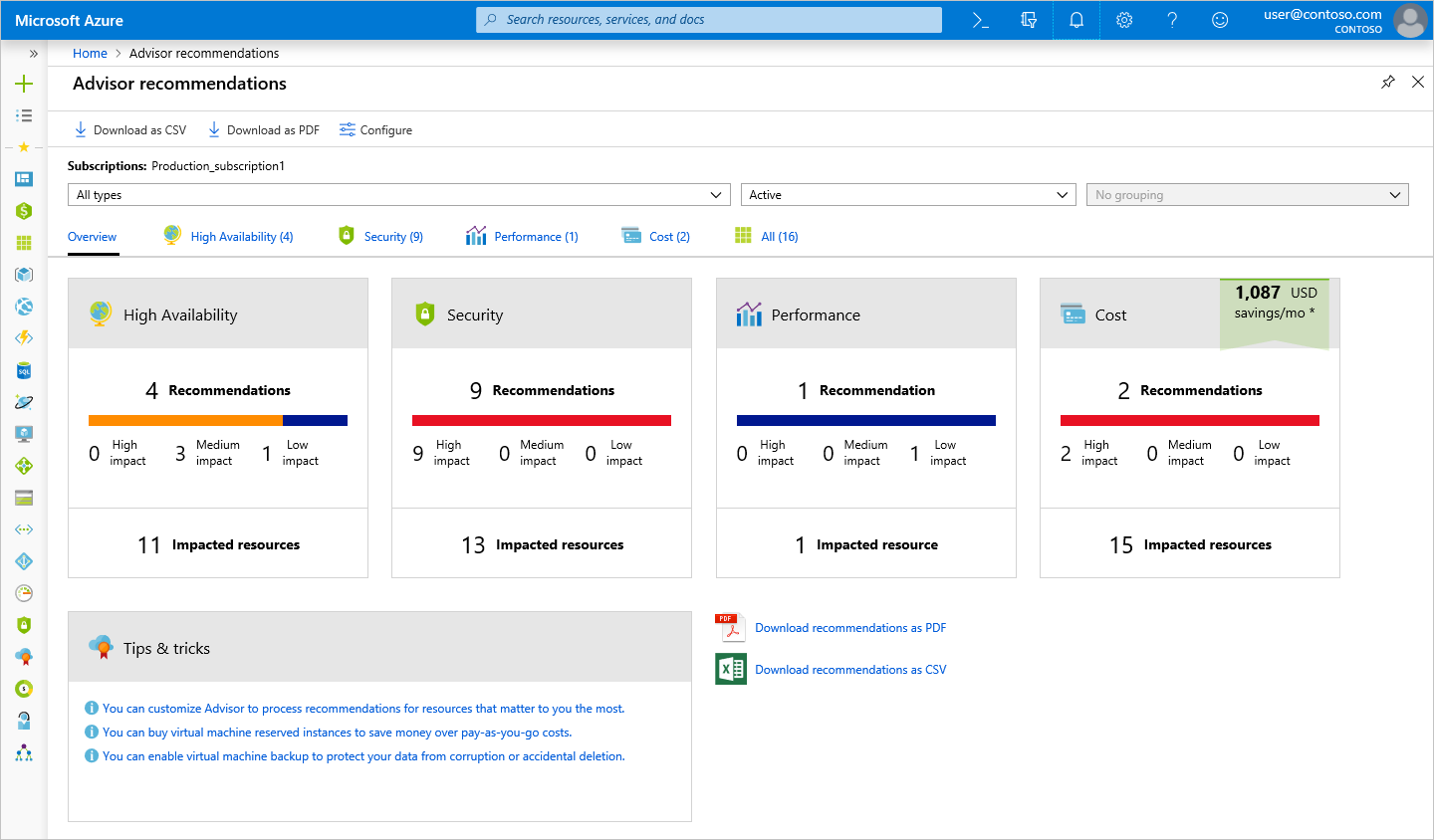
Feel free to reach out anytime with your Azure of Office 365 questions or queries?
Digital transformation is the process of cultural, technological and thought leadership innovation, that is required to ensure businesses remain competitive, relevant and able to survive. Let’s break that down and explain what I mean.
Click on the image below to see ALC’s range of courses that can help with your digital transformation journey:
This means allowing people within a business to develop and grow, by learning in a safe environment. We often call this Failing Fast. This helps to foster a culture within an organisation, that moves away from:
And move towards:
You can only innovate when you allow people to take risks. But in concert, you need to provide tools and an environment for continual fast feedback. This includes:
All these concepts and learnings appear again and again in many of the cultural change courses I run:
Click on the picture below to watch an awesome video from our DevOps Foundation course, covering Spotify Engineering Culture:
This means adopting the latest technological innovations, to help business leaders learn and act quickly. There are many examples:
It’s no surprise that at ALC, we’re focusing on these key technological innovations:
Click on the diagram, below to see an awesome video from the Enterprise Big Data Professional course on why we use Hadoop over SQL when dealing with Big Data:
This is the most critical. Leaders are the people in a company that pave the way for new things. Just like in music, they are the avant-garde, breaking new ground, failing fast and leading by example. They are skillful coaches that bring all their people with them on the journey. They lead through:
You’ll find these leadership traits are exemplified in the following courses for leaders:
The diagram below shows you the Scaled Agile Framework, of SAFe for short. Click on it and you’ll be taken to the FREE clickable version on their website:
If you have ever worked in a government department or a local council, there are very few examples of these digital successes. Why? I believe many leaders of governments, whether they be the lord mayor of a council or the elected minister, fundamentally do not understand digital disruption. They believe it is a phenomenon that only affects commercial entities and is not relevant to them. And the ones that do try and embrace digital disruption, don’t focus on cultural change, with leaders not leading by example.
Unfortunately, it is extremely relevant. I believe governments will be disrupted, just like every organisation in the world will be disrupted. Charities, councils, regulatory bodies, none of them are immune. In fact, they are the entities that are most at risk of being irrelevant. Why?
Because for every government service, there is are much better ways of delivering, by adopting the key tenants above and embracing digital transformation. This means, if enough people do not see the value in government services, they will protest, they will resist taxes and want to live in a place where the services are incredible.
We’ve seen trailers of this movie before:
Click on the diagram to show you how you digitally transform your government organisation using SAFe:
Check out my latest conversation on “Navingating Digital Disruption” on the New York hit show, #AskTheCEO with Avrohom Gottheil:
Your enterprise’s business processes and IT infrastructure are two of the most important elements for success and profitability. It naturally follows that you’ll want to have a strategy for developing your enterprise architecture. TOGAF is one of the most popular EA frameworks in use around the world. So what are the benefits of TOGAF and how can you apply it more effectively to achieve your business goals?
TOGAF is an open source enterprise architecture (EA) methodology designed to drive business efficiency in organisations. Widely used around the world TOGAF is a highly reliable framework EA professionals can apply to enhance consistency in their methods as well as communication.
TOGAF includes an established methodology, the Architecture Development Method (ADM). This is designed to help your enterprise plan the best route from A to B by taking potential problems, unique elements of your organisation, and other factors into account.
TOGAF is developed and updated by The Open Group, a non-profit organisation concerned with leading EA standards and certification for enterprises. Currently, at Version 9.2, TOGAF is now seeing its certifications accelerating around the world as enterprises become increasingly aware of its benefits.
TOGAF can be used to improve efficiency by ensuring your EA and EA professionals work to leading EA standards. No EA is static, and TOGAF gives you a methodology for constant evolution.
TOGAF is an open-source standard, which means organisations applying this methodology are free from the baggage of proprietary methods and systems. As a result, your enterprise could enjoy higher ROI, better utilisation of resources, and more versatility.
TOGAF isn’t a cure-all or prescriptive solution, and this is an advantage as it means you can apply it in a flexible way to suit the context in your enterprise.
TOGAF can be used to establish a clear baseline for your enterprise’s EA and in turn, create stronger business value in your enterprise.
TOGAF can give managers a better overview of the business landscape, improved understanding of how the EA constrains or empowers the business, and a clearer view of the implications of different action plans. Staff members also can get a clearer picture of the business architecture.
Enterprises could improve their strategy and investment planning processes by applying TOGAF.
Businesses can use TOGAF templates to streamline architecture governance and practice.
TOGAF could lead to agility and faster changes, lower complexity, stronger capabilities, and reduced management costs. Because you work to a clear set of ROIs, your enterprise could lower unnecessary expenses and raise efficiency.
TOGAF can allow you to refine development goals so they’re more accurate. This is TOFAF methodology is designed to incorporate the needs of teams into streamlined business practice in order to promote efficiency.
TOGAF could allow you to better align your IT capabilities with your development goals because you have the standards and language for planning and implementation.
Ultimately, TOGAF can help you scale your processes to take your enterprise to the next level. But how could organisations use TOGAF more effectively to achieve this?
Before implementing TOGAF, examine your business strategy and the direction your enterprise wants to move in. Once you’re clear on these, you can use them to define how you’ll use TOGAF to develop your EA. Your strategy and goals will inform the specific methods and techniques you’ll be drawing from TOGAF for your business. This is a reflection of the fact TOGAF isn’t a prescriptive system but a flexible one.
Use TOGAF to obtain a clearer picture of your business architecture. By using the methodology, tools, common vocabulary, and recommended standards, you can better understand what’s going on in your EA. This could help you develop smarter plans, address any issues or weaknesses, and adjust and deploy your EA so it’s closely aligned with your business goals.
Leverage TOGAF methodologies to create and refine development goals so they’re more accurate. This could help you and your team understand how to better perform the work and where more attention is required. You can then create a plan that factors in all the relevant elements. In turn, this creates a stronger basis for goal setting as well as hitting your targets.
A shortage of deep TOGAF expertise in the market could mean your enterprise lacks the right human resources for implementing TOGAF. If so, ensure you’re training EA professionals with the right TOGAF certifications.
TOGAF isn’t a prescriptive methodology. It could work best when you see it as an important link in the EA value chain and apply it in a flexible manner as appropriate for your enterprise. Avoid taking it too literally, and don’t use TOGAF as an excuse to neglect other key issues like setting KPIs for your EA staff. Apply the practices, processes, guidelines, and techniques in TOGAF in a flexible manner.
Your EA strategy could be met with failure if you don’t provide the right leadership. Executive management should champion TOGAF initiatives and obtain buy-in from the rest of the organisation, especially your EA team.
It can be beneficial to first clean up any existing legacy IT issues like duplicate systems, data islands, and inflexible infrastructure. Once you address these legacy issues to the point where you can create a baseline, your enterprise will be in a better position to start on future scenario planning for business targets.
TOGAF is a powerful methodology for everything from refining your EA to driving stronger business outcomes. Applied appropriately, it could allow your business managers to get a better view of the business landscape, support your strategy and investment planning, and allow you to refine development goals.
By understanding that it’s a flexible methodology, getting managers to champion it, and aligning it to your business strategy, you could reap the potential benefits of TOGAF in your organisation.
ALC Training is a leading Australian-based provider of accredited certifications to businesses and government. We can help your EA team get up to speed with Australia’s number one TOGAF training program. To find out more about our TOGAF 9.2 Level 1 and Level 2 programs, contact us now.
This blog is going to explain, in non-technical jargon, two things:
I was inspired to write this article after ALC Training released a FREE 20 minute Cloud Computing Mini-Course last week, where I personally take you through a fun and engaging cloud journey. It’s aimed at a non-technical audience, where you’ll learn the basic knowledge needed for all industry recognised cloud computing courses:
Why Use the Cloud?
Because that is the technology that powers how mobile apps work…..and it powers the entire app ecosystem:

And it also powers the largest social media platforms work:
It’s also how online shopping works:

And now it’s how core productivity apps work. I mean your Word, Excel and Powerpoint apps are all cloud-based:
And it also powers the biggest email systems:

You can store files:
It can also update software in cars:

In fact, it all started with web site hosting, at the birth of the internet, for most people, in the late ’90s:
Here is the first web site, created by Tim Berners-Lee…and yes…it’s still live. Click to the picture to visit:
What is Cloud Computing?
In simple terms it’s a new way of doing business, enabled by technology. Not just business, business, but also personal business.
It’s accessible via a store, or via a web browser, which provides lots of benefits:
In fact, every form of communication known to man, you can post somewhere using an app, and other people can view and interact with it.

But what really is the cloud?
In the technology world, we call it a platform. A foundation for hosting apps.
There are 3 types of cloud:
If you found this article interesting, and want to take your cloud knowledge to another level then check out my course. In partnership with ALC Training, I offer a 2 Day Cloud Foundation course for non-technical or semi-technical people. It’s a classroom-based environment where interaction, games, and fun are key learning tools.
Are you an entrepreneur, a project manager, an auditor, a talent acquisition specialist, a human resources professional, a marketing whizz….in fact anyone with a strong interest in the cloud….then this course is a good fit for you.
The best part is that it leads to an industry recognised certification, backed by APMG International……which shows up as a digital badge on your LinkedIn profile. Perfect for showing that your current employer is serious about cloud computing.
Interested in attending…..check out the dates, by clicking on the image below:
If the dates are not suitable, please reach out to our awesome team at ALC Training, and we can customise the course to your needs and bring to your location.
I hope you enjoyed this blog article. Have a great week.
P