Australian organisations continue to experience cyberattacks that have the potential to severely impact and disrupt business operations and customer value. While information security training courses can help employees address threats, many organisations are without these expertise. As such, a vast segment of these threats go undetected or are identified too late for a business to react effectively.
To address these threats, businesses need to be properly prepared. But many in Australia are unaware of what this entails. This has been compounded by the ever-changing cybersecurity landscape that sees new malware every week and continuously evolving cyberstrategies. As such, it is essential that companies do not only prepare for what they know is a threat but also endeavour to be ready for unseen cyberdangers.
Information security training courses are essential to ensuring a company’s information is safe and secure.
To help organisational leaders understand what they need to do, here are three fundamental steps when preparing for cyberattacks in today’s digital age.
Step 1 – Know your assets
In the face of an ever growing array of more complex hacker tools, the budget limitations facing companies are becoming increasingly salient. But cyber-related attacks are not going away, and the recent Australian budget highlights this, with the government investing over $200 million into its Cyber Security Strategy.
Unlike the government, most Australian organisations do not have a blank check to throw at cybersecurity, instead, they must think strategically. Most importantly, organisational leaders must identify the assets they need to protect and pinpoint the investments that can protect them.
Through a process of identification, an organisation can prioritise security areas that need investment as well as the security requirements for third parties that host your data. However, it is important to ensure you do not overlook the value of certain systems and processes. Take for instance, the normal administration systems. While many might view this as of little value, if your internal and external communication system is taken down, an organisation may be unable to engage with key stakeholders such as suppliers and customers.
Step 2 – Identify and analyse your cyberrisk
After defining your key assets, the second step is accessing your cyberrisk. This involves using technology, processes and personnel with information security training to develop a situational awareness of the types of risks your company faces.
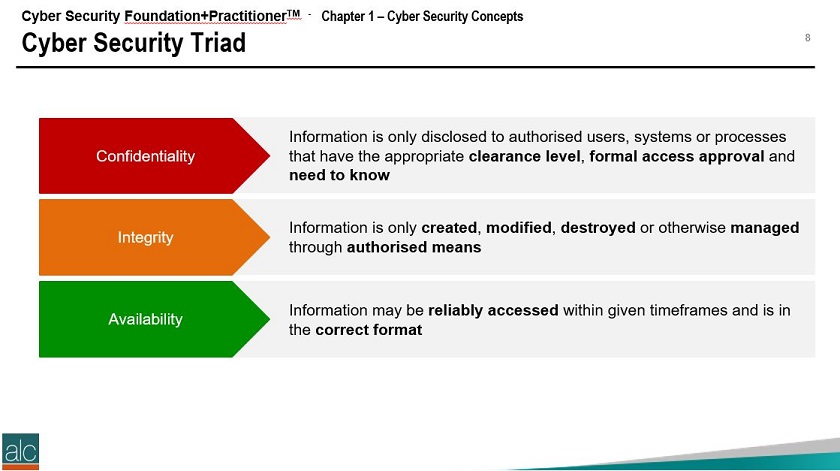
Building a strategic plan based on these three factors can help maintain the confidentiality, integrity and availability of your informational assets. On the other hand, it is also essential to be aware of the specific risks that face your industry. For example, Australia’s medical sector has been presented with a number of unique challenges that require distinct approaches.
According to PricewaterhouseCoopers, the rise of telemedicine, social media and mobile sharing has transformed the relationships between businesses and their customers. It has also made a significant segment of patient data accessible online, which has ushered in new cybersecurity risks.
 Making sure security is a prime focus is essential.
Making sure security is a prime focus is essential.Step 3 – Make awareness and hygiene a priority
To ensure that your assets and the specific risks that face your company are dealt with correctly, the first step is identifying internal risks.
One of the most important factors to this is employee hygiene. This refers to making sure employees are aware of the sensitive information they have access to and their role in protecting it.
One way to accomplish this is through proactive and ongoing training. Educating staff on how to respond to an incident can mitigate the effects of a cyberattack. They should know who to call, who is authorised to speak for the company and what role they will play in the following investigation.
Fortunately, training providers such as ALC Training can help deliver best practice workshops that can help employees meet the basic requirements of cybersecurity hygiene. If you would like to know more, talk to a representative today.