



I have been in the infosec sector for over three decades and have seen the rise and fall of demand for IT and security professionals on a number of occasions. Y2K, the dot com bust and the GFC did not help our industry. Currently, we are on an upward trend, delivering training across Australia, NZ, Malaysia, Singapore and Dubai. I have seen year-on-year growth as people take up the call to either upskill, try to get a foot in the door or just learn about on-trend topics, such as cyber security, architecture, cloud, big data, artificial intelligence, digital forensics or incident response.
ALC recently added privacy to our portfolio by partnering with the International Association of Privacy Professionals (IAPP) and we’re making great inroads due to the pent-up demand in Australia and New Zealand. At the recent IAPP conference, the key message emerging from presenters, is one of accountability – having a key individual within an organisation drive the privacy agenda forward; it is all about privacy by design. And no wonder, every week, there is an article on a new privacy breach, quite often coupled with staff dismissals and a hefty fine.

Our cloud portfolio is also strengthening. ALC made a strategic decision to add Certified Cloud Security Professional (CCSP) to the portfolio in 2017, along with other cloud courses, and Australia now has more certified CCSPs compared to Germany! Running the numbers, we can proudly say we have trained two thirds of those certified in Australia alone. For those who hold a CISSP or have anything to do with cloud, I highly recommend the (ISC)2 CCSP® certification.
So is it all hype, or is there a genuine need for training? In reality, it’s a little hype, but also a genuine need to fill a gap. Increasingly, we have delegates cite several reasons for becoming certified: personal challenge, company requirement, or simply to learn. Many delegates are from organisations that are typically under-resourced when it comes to security and privacy, expecting miracles with existing staff numbers.
Remember, security and privacy are solved by people, process and technology. Therefore, it is everyone’s responsibility. We need effective awareness training and to skill those people on technologies, to look after security in their own domains – rather than expecting a security professional to become a master of all trades. There is a plethora of courses out there to do precisely that.
ALC’s focus is to deliver industry recognised training and certifications that are needed now and into the future. ALC has always been at the forefront of Information Security education since our very first course on Information and System Security in 1995. Our flagship set of courses on SABSA® security architecture and industry standard certifications such as CISSP® and CISM® are designed to meet the needs of the security professional. (FACT: Did you know ALC is an ISACA Training Partner!) Also, in the past three years we’ve placed a very strong focus on addressing the needs of newcomers to Cyber Security to help enable the industry to broaden its skills base with our Cyber Security Foundation+Practitioner Certification.
Cyber Security is a prominent, highly-regarded profession offering many varied career paths. The ALC Cyber Security Portfolio offers a formal route to becoming a recognised and respected cyber security professional through a modular program of certificate and non-certificate courses. Whatever stage you are at in your career, or if you are an Executive in need of improving capabilities within your organisation, we are here to help you, your team or your company, locally and worldwide.
Get in touch with our team to see how we can assist to deliver optimal training suited to your needs.
Peter Nikitser, Director of Cyber Security – ALC
Believe it or not, Office 365 now contains 27 separate apps that are provided by Microsoft. Many of these apps are provided with advanced security features. Clearly managing these security features within each admin tool is a complex and onerous task. So Microsoft have moved as much security as possible into the Office 365 Security & Compliance Centre. This is now the central place to manage the majority of security functions in Office 365.
Click on the diagram below to link to the Microsoft TechNet article describing all the key Office 365 services:
You can augment this list by adding third-party apps that are available in the Microsoft AppSource app store. You can also incorporate various Azure services that integrate with Office. One service that is already included, is Azure Active Directory.
Azure Active Directory or AAD, is a mandatory service that manages all the authentication and authorisations in Office 365. It integrates with your existing corporate Active Directory, which probably lives in your data centre (on-premise), using a service called AAD Connect. For companies that have very complex requirements around transferring data between your on-premise Active Directory and AAD, you can use the Microsoft Identity Manager product and the Active Directory Federation Service.
Here is a great link to a video that outlines some of the basics of Active Directory:
It becomes quite technical towards the end of the video, so just close it down, once you have the knowledge you need.
Understanding Active Directory is key to understanding the fundamentals of how the Office 365 Security & Compliance Centre works, so check out my 2 day course where we cover all the basics, in non-technical language, so that anyone can start security their Office 365 tenancy:
Not only do we cover AAD, but we also run through:
Let’s pick out a couple of my favourite Office 365 services…Flow.
Flow is a product that allows you to integrate various cloud services, providing a platform for automating many of your tasks. It’s a competitor to IFTTT.com, which stands for If This Then That, which provides a similar set of services. For example, if an email comes into your inbox from a customer, there may be a series of manual tasks that need to be undertaken to start servicing that customer. This can be automated and free up your time to focus on talking with customers, rather than having to do repetitive manual tasks.
Click on the graphic to be taken to a video outlining potential uses of the tool:
Now, let’s look at some of the key features of Data Loss Prevention
If want to know more about Office 365 services, please reach out to me on Linkedin. Click on the image below to see my profile and start reaching out….
Last week I was running a course in Auckland, where I demonstrated the Office 365 Security & Compliance Center. The great thing about this new tool, is that it is policy-based, interactive and extremely visual.
What does that really mean?
You need to firstly determine the important information around your corporate security posture. Then you can translate this into the Security & Compliance Center, via a series of rules. This allows you to maintain compliance with the law, a regulated industry and your company polices.
Once the policies are in place, you have a series of interactive visualisations and methods, for determining how end-users are using the platform and whether they are in breach of your policies.
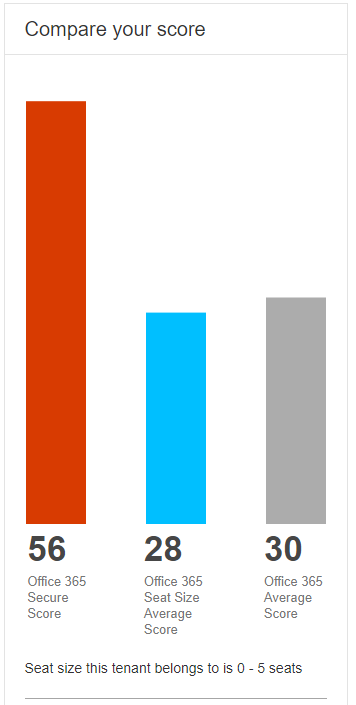
Here is a simple example. I always recommend starting with the Secure Score, once you have your Office 365 tenant running. You’ll need an E1 / E3 or E5 licence to be able to follow this through:
Don’t forget to Save the customised home screen and then access the tile by clicking on Go to Secure Score:

Depending on the security posture of your organisation, you can choose to increase or decrease your target secure score. A way of benchmarking this is to have a look at other clients with a similar profile, using the comparison bar chart:
The types of recommendations the tool makes can include the following:
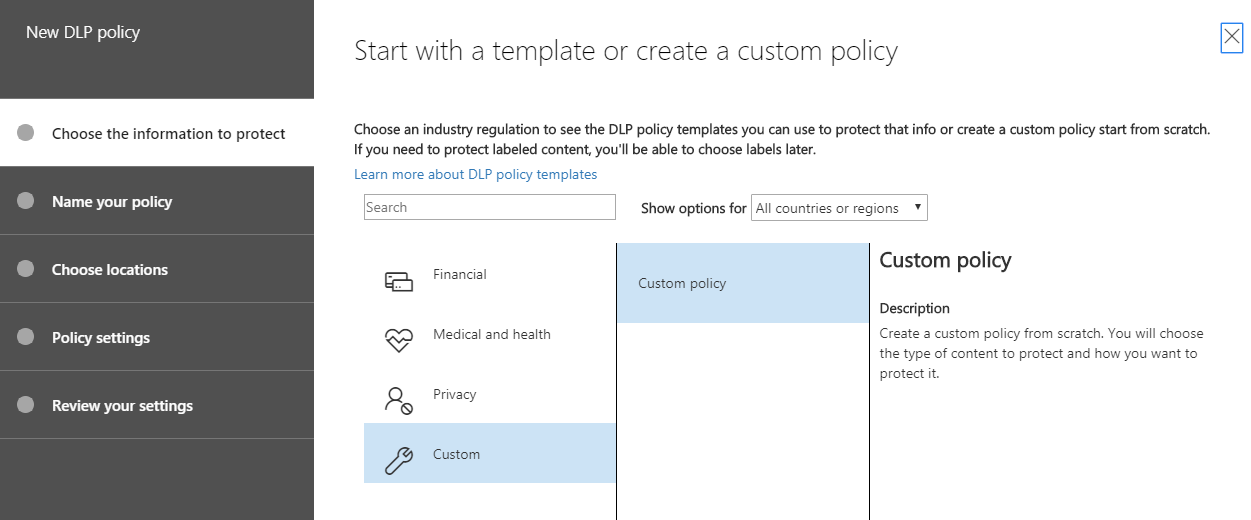
Other incredible features include setting up Data Loss Prevention Rules, using pre-defined templates that align to geography and industry:
Another feature, is to set up the Data Governance Rules to ensure that you retain in-line with legislation and ensure it is securely deleted after that time:

Obtaining all the various compliance reports associated with Office 365 and Azure for a particularly geography and industry:

Lastly, here is a great tweet on how to setup permissions in the Office 365 Security & Compliance Center:
Ever wondered how to setup permissions quickly in the #Office365 #Security & #Compliance Centre https://t.co/l0d8oDRVIV #Cloud @ALCGroup -check out our Office365 course for hands-on #trainingdemos https://t.co/xzDclt3EgY #cybersecurity pic.twitter.com/qpqDtY3wAG
— Paul Colmer ☁ (@MusicComposer1) 8 March 2018
The trick with permissions, is to understand the various roles that you can assign to groups and users, and how permissive or restrictive those roles are. If you need to tailor the roles, keep the original defaults, and simply create a new role. Remember to create a detailed description of how it differs from the original default role.
If you’re interested in learning more about the Office 365 Security & Compliance Center, there are plenty of great links on TechNet to get you started. And if you feel you need something a little more, check out our face-to-face classroom training course on Office 365 Security & Compliance. The ‘pièce de résistance’ is where I interactively demo the tool and coach you through the latest security best practices.
And finally, here is a great iconic picture to share, showing the wonderful city of Auckland and the great country that is New Zealand:
Oh…and I just must share the best Auckland pic of the Ed Sheeran concert too!!
P.S If you’re not sure your cybersecurity knowledge is up to scratch, take our cybersecurity quiz to see how you measure up.
It was just last year that the Ponemon Institute and IBM announced startling global data breach statistics. According to the organisations, in the Cost of Data Breach Study: Global Analysis study, the average cost of a data breach grew 23 per cent from the same report in 2013.
The COBIT 5 framework has long been seen as a leading framework for the effective governance and management of IT.
This study analysed 350 companies across 11 countries, also finding that the average cost incurred for every record lost or stolen grew from 2013, rising from US$145 to US$154.
Interestingly, Gartner explained that 75 per cent of enterprise information security budgets will be allocated solely for the purposes of rapid detection and response in 2020, a step up from the 10 per cent in 2012.
What’s more, the organisation also noted that worldwide spending on IT security is increasing as government initiatives, increased legislation and data breaches continue to mount. Interestingly, digital business is another leading factor in security spending growth.
“Interest in security technologies is increasingly driven by elements of digital business, particularly cloud, mobile computing and now also the Internet of Things, as well as by the sophisticated and high-impact nature of advanced targeted attacks,” Elizabeth Kim, research analyst at Gartner noted.
It’s clear that organisations and professionals alike need to start thinking seriously about risk management, especially with data breaches showing no signs of abating, and organisations increasingly funnelling funds into security technologies and processes.
Of course, there’s always a need to balance a focus on security with the actual running of the business. This is where COBIT 5 comes into play.
The COBIT 5 framework has long been seen as a leading framework for the effective governance and management of IT, especially at the enterprise level. The real value of COBIT 5 lies in just how how broad the applications are. The associated tools, guidance and resources can help with things like regulatory compliance, risk management and of course information security.
COBIT 5 goes beyond risk management solely with regards to IT security.
COBIT 5 also goes beyond risk management solely with regards to IT security. There’s a misconception in the IT industry that all risks are security-related, even though there’s actually a significant number of scenarios and possible IT issues that need to be considered.
This is where COBIT 5 for Risk can prove a useful consideration for IT professionals and organisations alike. It’s designed to offer introductory as well as practical coverage of all aspects related to the management and governance of risk within the wider organisation.
Training with the experts is always the best way to ensure either you or your employees have the knowledge needed to utilise a framework. This means getting in touch with ALC Training.
ALC offer a number of different courses focused on some of the most capable and proven frameworks available. SABSA, ITIL and PRINCE2 are just a few of the others available that can certainly help individuals to up-skill. This isn’t to mention the COBIT 5 offerings.
Reach out to ALC Training today if you’d like to get started with a framework that can really help with risk management. In turn, organisational security will seem a far less daunting prospect.
Security risks aren’t likely to decrease at any point in the near future, and organisations need to be prepared by equipping professionals with the right skill sets.
Cybersecurity. It can be an intimidating prospect to get your head around, especially when IT isn’t in your job description. However, digital infrastructure has quickly become the dominant foundation upon which businesses are operating. While the digital sphere offers countless advantages and opportunities, it also brings with it a new threats.
Over the past few decades, technology has become a critical component to business success.
No company can survive, let alone thrive, without making good use of the technology solutions and tools available to them. Despite this, many organisations are still struggling to achieve maximum business value from their IT specialists.
With that in mind, here are three reasons why your organisation is failing to maximise the performance of its IT department.
Insufficient training and support
The information technology sector is constantly evolving, with new challenges and opportunities arising every day. In order to keep up with these changes, your IT department requires sufficient training and ongoing support.
Providing your IT department with opportunities to participate in specialised training courses in critical areas such as information security can ensure that they are constantly on the forefront of breaking industry developments and delivering true value to your enterprise.
Underfunding and poor integration
According to a Gartner survey released earlier this year, Chief Information Officers in the Asia Pacific and Japan region are planning on growing their IT budgets by 0.9 per cent this year. However, even with this increase, many IT departments will still be significantly short of the funding they need to operate efficiently.
That same Gartner survey found that modern IT departments are only receiving 65 per cent of their funding from within the conventional IT budget. The rest is coming from other business areas, such as marketing, sales, operations and R&D.
Gartner Vice President Andy Rowsell-Jones has warned that this "high level of unconventional funding from outside IT" could potentially lead to integration issues and governance problems in the long term, suggesting that many organisations need to rethink their approach to this critical area of business.
Lack of leadership
In order to deliver to its fullest potential, your IT department needs to be helmed by a strong leader or leadership team which has a thorough understanding of your business and strategic goals.
It's also important that businesses pay proper attention to IT leadership, bringing them into the fold on important decisions and keeping them informed on strategic decisions and planning. This will ensure that your IT department is optimising internal strategies in line with the wider direction of the organisation.
The breakout television show of 2015, Mr. Robot, follows Elliot Alderson, a young and anti-social computer engineer secretly taking part in a vigilante hacking group. The show has received praise for its original and socially relevant subject matter, alongside the realism represented in its hacking scenes.
With the fourth and final season of Mr. Robot recently available through TV on demand, let’s take a look at one of the technological marvels showcased in the first season. Below, we’ll discuss a prominent hacking technique performed by Elliot, the real world comparisons and how this may affect your online activity.
TOR is a system for anonymous communication developed originally for the US Navy.
In the opening scene of the first episode, we are introduced to Elliot and his extraordinary computer abilities. During a conversation with the owner of the cafe he sits inside, we learn that for a number of weeks, Elliot has been monitoring network activity within the business. Our computer hacker explains that he breached the network by taking control of TOR exit nodes and decrypting the anonymous traffic.
TOR, as many of us know, is an evolution of a system for anonymous communication developed originally for the US Navy and further advanced by DARPA in the late 1990s. While TOR is touted as a completely anonymous network – famously known for credit card fraud, money laundering, black market drug trades and the rise of Bitcoin – there are a few areas of weakness that can lead those with limited IT security training into very dangerous territory.
There’s some confusion around what the term anonymous actually means. It would be a grave mistake for anyone with only a basic knowledge of network security, proxies, exit nodes and anonymous browsing to download TOR and believe everything they are doing is hidden from others. Despite being touted as the go-to anonymous browser, the level of privacy offered by the software quickly dissolves in inexperienced hands.
Exit nodes within the TOR network work similar to a proxy server – where indirect connections are made between various network services – allowing anyone monitoring the traffic in these nodes to capture and potentially decrypt information being transferred. Of course, it’s incredibly easy to find an entire active list of TOR exit nodes online in seconds, meaning you’re able to choose which node you use as an exit relay.
Whenever you take the risk of doing something illegal online, there’s a very high chance that someone may be watching.
There are other access points within the TOR network, such as groups of middle relays for information to pass through that allow the data to bypass censorship concerns with little risk to the owner of the relay. Bridges – not officially listed as part of TOR – are crucial for navigation around blocked IP addresses in countries with strict policies on freedom of internet use.
The moral of the story on Mr. Robot is simple – whenever you take the risk of doing something illegal online, even downloading a TV show, there’s a very high chance that someone may be watching.
Anonymous browsing is never truly anonymous, and those who believe they are safe will no doubt find themselves in a similar situation to the nefarious owner of the television coffee shop – visited by a swarm of police officers following an anonymous tip and a horde of collected evidence.
The expert team at ALC Training value the importance of knowledge and expertise in the IT industry and offer a range of courses across framework and risk assessment techniques, right through to information security training and higher-level training for executives and decision makers.
To learn more about what our expert training can do for you and your business, reach out today.
The recent data breach of the Democratic National Committee (DNC) shows not only that governments aren’t above being hacked, but that the greatest opponents may be foreign governments themselves.
The scope of government-funded cybercrime was recognised in September, 2015, when a deal made between the US and Chinese presidents called for neither government to knowingly conduct or support the theft of intellectual property through the use of cybercrime tactics.
 Securing your network is crucial to protecting your company’s data.
Securing your network is crucial to protecting your company’s data.In a report released by FireEye, the IT security company suggests that public reports exposing the level of involvement China has in economic espionage gave the US government sufficient knowledge and support to confront China about the level of cybercrime.
Russia joins the cyberwarfare battlefield
The report from FireEye indicates a steady decrease in Chinese-led cyberespionage. However, that hasn’t stopped Russia-based hacker groups from positioning themselves at the front of this global security war, highlighting the need for increased IT security training.
In a recent post on Peerlyst – an online information security community – Jarno Limnell of Aalto University in Finland detailed how increased cyberaggression from Russia could have terrifying implications further down the line if not met with resistance.
“Russia has the ability and will to carry out denial-of-service attacks, develop sophisticated malware, and exploit unknown software vulnerabilities,” he noted.
In contrast to China – where cyberespionage has shown a large direction toward economic disruption – Russia-based hackers are more led toward scouting networks and determining the feasibility of future attacks.
“Russian cyber activities focus primarily on intelligence gathering and military reconnaissance of critical infrastructure networks. It has to be remembered that today’s intelligence operations enable tomorrow’s actions, and Russia is mapping networks to determine the resources necessary for future attacks,” Limnell wrote.
Democrats lose their trump card
Following the data breach of the DNC – in which hackers spent months within the system to target the opposition research on Donald Trump – Russia-based cyberattacks were declared the greatest threat to the United States’ national security, according to Director of National Intelligence James Clapper.
A single record of healthcare or education data is valued at US$355 and $246 respectively.
Choosing the appropriate security framework is an essential first step to addressing this type of threat, as a security framework will provide a common language that can be shared by professionals.
This means that any potential network attacks or undesirable situations that may arise can be handled swiftly and with clear communication – providing a solution to the problem before the issue can exacerbate itself.
Data breaches across all industry
For any company, no matter how small, a loss of data can be a costly thing. According to research sponsored by IBM and conducted by Ponemon Institute, while Australia is one of the two least likely countries in the world to experience a data breach, having your business’ data compromised is still a financial nightmare.
The report estimates the cost of data breaches across a number of industries – with a single record of healthcare or education data valued at US$355 and $246 respectively.
With the lowest average figure belonging to the public sector at $80 – and data breaches reported by Symantec exposing up to 191 million records in a single attack – it’s clear that this kind of network assault can cause serious damage regardless of the industry.
 Choosing the right security framework is vital to the health of your business.
Choosing the right security framework is vital to the health of your business.The framework of security with ALC Training
Keeping yourself at the forefront of security technology is as crucial as deciding on the right security framework. Offering expert knowledge across a number of essential framework courses, choosing ALC as your IT governance training provider is the first step to advancing your career in IT.
Ensure that your business has the best advantage when it comes to preventing data breaches or unwanted access to your network – get in touch with ALC Training today.
When Symantec released its Internet Security Threat Report in April, 2016, a number of disturbing trends were highlighted in the world of information security.
Some of the key trends that were identified in the report covered large data breaches in companies, an increase in zero-day vulnerabilities and the growing use of ransomware for extortion techniques – highlighting the importance of information security training.
Stolen data not fully disclosed
Large businesses have always been a target for cybercriminals. When a company holds a lot of data in its network, valuable information to either the business or potential competitors, it can become a clear target for an attack.
The report notes that at the end of 2015, the largest data breach ever publicly reported – a total of 191 million records – rounded out a year of nine mega-breaches. This level of data leak is defined as containing more than 10 million records, but this figure isn’t the most unsettling discovery in the report.
Symantec estimates that the number of companies that chose not to disclose the amount of records lost in data attacks increased 85 per cent in 2015, with the excluded data moving the total figure of personal records stolen to over half a billion.
It doesn’t matter why the companies decided not to release the detailed extent of their data breaches; the lack of information supplied provides a painful blow to internet security. The crux of effective security is knowledge, and the lack of clarity around the data breaches means a lessened ability to react and adapt to the methods used by cybercriminals.
Four of the five most popularly exploited zero-day vulnerabilities were discovered in Adobe Flash.
The hunt for zero-day vulnerabilities
A zero-day exploit is a flaw in a piece of software that is unknown to the developers and undisclosed to the general public, receiving its name due to the window of time available to patch or implement a response procedure.
The majority of zero-day vulnerabilities are found in very common and popular applications – four of the five most popularly exploited zero-day vulnerabilities were discovered in Adobe Flash.
Despite the large amounts of unique and emerging malware discovered in 2015, data from McAfee Labs estimates backdoor and botnets only account for 2 per cent of total network attacks. However, malware coders have always been particularly fond of these types of exploits, as it allows them to utilise other means of network entry.
Cybercriminals who write malicious code can incorporate this into a website, causing anybody who visits the page to activate a vulnerability in their web browser. When you consider how many popular web browsers we really have, having continuous exploits in one of the most widely used is a worrying prospect for cybersecurity.
 Locking a company out of their data is a popular ransomware method.
Locking a company out of their data is a popular ransomware method.Big data held at ransom
Crypto-ransomware has moved to the forefront of security statistics lately, as we see hackers placing a heavier emphasis on the encryption of data over the more traditional method of locking the user from their computer screen.
This type of attack remains extremely profitable to hackers, and 2015 saw a move away from the more traditional targets of PC’s toward Mac, Linux and mobile phone users.
Despite a steady decline in traditional ransomware in 2015 – with February and June providing the highest figures of recorded usage – crypto-ransomware grew from around 10 to over 50 per cent from July to December.
It makes sense why this type of attack is popular with hackers – locking someone out of their own data provides little option for recovery outside of paying the demand. Unlike a credit card or bank exploit, where monetary loss can be replaced and insured, recovery of data can potentially be impossible.
The number of infected apps listed in the Symantec report total as high as 4,000.
Life imitating art and Xcode exploits
One crypto-ransomware tactic being employed by hackers is to increase pressure on a victim by destroying the encryption key after a set amount of time – causing the locked data to be lost forever. We’ve seen this method popularised on the television show, Mr Robot, where a similar situation of data ransomware led to the total collapse of the world economy and global riots.
Previously thought to be immune to attack, users of Apple products should be more vigilant than before – a malicious code known as XcodeGhost has been discovered in Xcode, Apple’s integrated development environment.
The number of infected apps listed in the Symantec report total as high as 4,000, with victims opening themselves up to a range of attacks once they’ve installed the software.
After a user downloads and installs one of the infected apps, their data is uploaded to a central command server and allows the hacker to perform a terrifying variety of actions, including generating false alerts to steal the username and password of the victim and remote opening of specific websites, potentially leading to further infection if coupled with a zero-day exploit of a web browser.
Arm yourself with knowledge to limit the risk
It’s imperative to the health of a business that the scope of exploits and malware be understood. ALC offers a range of IT security training courses including SABSA security architecture, CISMP and CISSP credentials and a selection of security awareness courses.
To learn how effective training can help safeguard your business, get in touch with ALC today.
On the bus trip to enjoy your shopping, a lovely young man sits next to you.You strike up a conversation and are happy to find you have similar interests. He also owns a dog, the same breed as yours, and he even demonstrates a love of the same films and sports.
You’re surprised to find out that you both grew up in the same area of the city, and you give the young man your phone number when he asks if you’d like to see the new Star Wars film next week. As you get off the bus, you wave goodbye and carry on with your shopping journey.
Before you can make your first purchase that day – perhaps even prior to entering the shopping centre – your email and social media accounts are compromised and your bank account is emptied.
 Information security training can protect you from cybercrime.
Information security training can protect you from cybercrime.Congratulations. You’ve become another unsuspecting addition to the statistics of social engineering.
Emotional extortion of information
Humans have long been the easiest targets for anyone wishing to compromise an information system. We don’t actively seek to accuse everyone of deception – if we did, our daily lives would be a paranoid mess – but this noble part of our psyche is also its greatest opportunity for exploitation.
Hackers – or anyone wishing to manipulate another person into revealing something – employ these tactics by targeting the vulnerabilities in our emotional response. In the example above, we see a few pieces of common password information change hands; pets and their breeds and names, favourite films and sports, and the area you grew up in.
By giving the hacker the bonus information of your phone number, they have everything they need to attempt a password crack on your accounts.
Humans have long been the easiest targets for anyone wishing to compromise an information system.
Passwords appearing closer to sudoku
SplashData has complied it’s annual Worst Passwords list in a continued attempt to bring light to the lax security around many individuals’ security. According to the data, “123456” and “password” are still the two most commonly used, with the rest of the list looking equally shocking.
As websites and apps demand greater security – with most passwords now requiring 8 digits or more – “12345678” has risen to third place, showing that, despite the attempt for increased protection, users are still falling short on their side.
Also on the list were the familiar sports themes of “football” and “baseball” alongside newcomers “letmein”, “passw0rd”, and “starwars”.
The faceless crime of identity theft
But even with a weak password and a friendliness toward strangers on the bus, you may still be wondering what anybody could want to break into your life for.
Identity theft can lead to hackers opening false bank accounts or making online purchases in your name. Even worse, recent scandals show that our most private photos and information in the cloud is able to be compromised. Blackmail of any sort can lead an individual to divulging political, business, or individual information.
A report by software company Symantec revealed that more than 550 million identities were exposed online. Looking at this figure, it’s clearly more important than ever to ensure your online identity and information are kept safe from attack.
Protecting the information core
Your brain is the most powerful weapon against cybercrime. By recognising the potential warning signs of social engineering techniques, you can keep your identity and financial details secure.
Effective training is one way to identify and eliminate these social engineering threats. Reach out to ALC Training today and find out how information security training courses can turn your brain into a mental Fort Knox.
Human psychology is a remarkable thing. How humans behave, how they interact with each other, what and who they trust – all of these can be tools for someone attempting to compromise network security. Understanding human behaviour or thought patterns and exploiting this knowledge to control or guide the actions of an individual is known as social engineering.
Social engineering tactics can involve all kinds of manipulative behaviour – a scam reported by the Australian Communications and Media Authority in 2016 discovered fake messages sent from seven leading banks. This event highlights the need for two-factor authentication on the internet, with a 2015 Verizon Data Breach report stating the effectiveness of this measure – it is the recommended strategy for 24 per cent of all security incidents.
Most of us are familiar with email spoofing – you receive an email from a friend that contains an exciting or alarming subject line, shortly followed by another email from the same friend urging their contacts not to open the last one.
Nobody can completely resist manipulation under the right circumstances, and this idea is the backbone of social engineering.
In 2015, 528 mobile phone vulnerabilities were discovered, a 214 per cent increase over the figure in 2014.
The 2016 landscape of cybercrime
Symantec recently released its 2016 Internet Threat Security Report, with the extensive collection of data revealing a number of new methods hackers are incorporating into their attacks. One of the alarming increases seen is the amount of information that is used and collected for the purpose of ransomware.
The report states that in 2015, 528 mobile phone vulnerabilities were discovered – a 214 per cent increase over the figure in 2014. While the total figure of new vulnerabilities saw a 15 per cent drop in 2015 from the previous year, the amount of zero-day vulnerabilities increased 125 per cent.
This would seem to suggest that increased deadline demands on technology programmers is forcing them to unleash applications to the market without putting them through proper testing.
As we move toward a future that looks to incorporate things like smart cities and utilities that are connected to the cloud, it's timely that we begin addressing these sorts of software vulnerabilities before the data taken from them is locked and used for ransom.
Social engineering increases
Another trend emerging is that hackers are using more personal techniques to compromise a system and gain access to information. The amount of websites found hosting malware decreased between 2014-15, with only 1 in every 3,172 sites discovered to contain the malicious software.
This isn't exactly new, however; as virus detection software has proved itself more capable, social engineering has accounted for an increasing amount of cybercrime. Instead, hackers are finding that the easiest way to penetrate a system is from the inside, using a business or company's own employees to their advantage.
Our social lives are also being pulled into the mix, with cybercriminals using methods that appeal to our need for popularity and to be noticed. As the technology to digitally protect a system advances, we could see fewer attempts to infect a network through traditional methods – requiring security training to adjust itself accordingly.
One scam noted by Symantec promised a large amount of Instagram followers, which tricked users into revealing their passwords. Other attacks included the impersonation of a bank via text message, and a fake tax office email that attempted to trick individuals into opening a malicious attachment.

Preventative training with ALC
ALC offers a range of information technology training courses, designed to teach those who have access to your network the warning signs that they may be targeted by a cybercriminal. The information security awareness programme details common computer and email viruses, what to do if you suspect an attack, and internet scams and phishing.
To equip your business and employees with the knowledge and tools they need to prevent a security attack before it happens, get in touch with ALC Training today.